
SaaS Churn Reduction via Product Engineering
Mar 27, 2025
Every SaaS business faces the challenge of customer churn – losing users before they can deliver long-term value. While some churn is inevitable, a significant portion is preventable with well-implemented SaaS churn reduction strategies. ...
read more
Startup Product Development: Avoid Pitfalls
Feb 28, 2025
Launching a startup is an exhilarating journey, but the path to building a successful product is riddled with challenges....
read more
Off-the-Shelf vs Custom Software: What You Must Know
Feb 11, 2025
Off-the-shelf software solutions often appear as cost-effective, quick fixes for businesses looking to digitize operations....
read more
Why Invoice Automation Is a Smart Business Move
Nov 12, 2024
For finance and procurement teams, processing invoices is often a time-consuming and error-prone task. ...
read more
Low-Cost Mobile App Dev: Smart Outsourcing Tips
Oct 01, 2024
Having a mobile app for your business today isn't just a luxury, but essential. However, the costs associated with mobile app development can be a significant burden, especially for small businesses and startups....
read more
Predictive Churn Analytics for Better C-Suite ROI
Aug 02, 2024
In today's competitive business environment, retaining customers is more critical than ever. ...
read more
Fix API Rate Limits with Smart Throttling Techniques
Jul 26, 2024
APIs are the backbone of modern software development, enabling seamless communication between different software systems....
read more
Software Implementation Plan | Key Considerations
Jun 11, 2024
The successful implementation of software systems has become a critical factor in driving organizational growth and competitiveness....
read more
How to Fix “The Developer of This App Needs to Update It to Work with This Version of iOS”
May 29, 2024
Are you getting the dreaded "The developer of this app needs to update it to work with this version of iOS" message? It’s like your app is throwing a tantrum, demanding a shiny new upgrade. ...
read more
IaaS Adoption Tips | Cloud Engineering Services Guide
May 20, 2024
Businesses today face increasing pressure to innovate, adapt, and deliver value to customers faster than ever before. ...
read more
5 Statistics That Will Make You Want to Build a Web App, Today!
Dec 29, 2023
The decisions made by ISV professionals carry profound implications for the future of their organizations, but also for the software landscape as a whole, given their ability to create software products that can disrupt the market....
read more
Brownfield vs Greenfield: Choosing the Right Path for Modern Software Development
Dec 21, 2023
The software landscape is a swiftly changing terrain, demanding agility and foresight. Independent Software Vendors (ISVs) often find themselves at a crossroads, contemplating the choice between Brownfield vs Greenfield software development....
read more
Bitbucket vs Gitlab vs Github – What Should be Your Go-To in 2024?
Dec 20, 2023
When it comes to collaborative coding, the battle of GitHub vs GitLab stands tall and plays a huge role in shaping the product engineering landscape....
read more
Predictive vs Adaptive Dev: Choose Your Strategy
Dec 04, 2023
Choosing the right product development strategy is a critical determinant of project success. The decision between Predictive and Adaptive development approaches requires an expert understanding of their intricacies. ...
read more
DevOps vs Waterfall: Why Agile Wins Every Time
Dec 04, 2023
Choosing the right software development methodology is crucial for success. While the Waterfall model has been a longstanding approach, its limitations have become more apparent in today's fast-paced and ever-evolving industry....
read more
Solve Issue Management Challenges with ServiceNow Managed Services
Nov 28, 2023
The efficiency of issue management has always stood as a critical benchmark. Here, ServiceNow emerges as a game-changer...
read more
Warehouse Automation for Peak Order Season Prep
Nov 28, 2023
Navigating the peaks of e-commerce demand is both a revenue boon and a logistical challenge....
read more
Master Node.js & Microservices for Live Data
Nov 23, 2023
The demand for real-time data processing has become a linchpin for success. Independent Software Vendors (ISVs) are beginning to recognize the potential of microservices and Node.js in achieving unparalleled excellence in real-time data processing. ...
read more
React vs React Native: Which Should You Choose?
Nov 20, 2023
The choice between React and React Native has become a pivotal decision, especially for Independent Software Vendors (ISVs)....
read more
Tailored Software Solutions in IT Strategy
Oct 25, 2023
The strategic utilization of IT resources stands is important for success. Among the numerous components that constitute IT strategy...
read more
Websites or Web Apps? What’s Right For You!
Oct 20, 2023
Choosing between a website or a web application for your digital platform strategy can often seem like a perplexing decision....
read more
Node vs React vs Angular: A Comparative Study
Oct 17, 2023
In the dynamic world of front-end web development, selecting the right JavaScript framework is akin to choosing the perfect tool for a complex job....
read more
From Code to Compliance: Unpacking the PHP 8.2 Update
Oct 12, 2023
When it comes to making your mark in the realm of Independent Software Vendors (ISVs), innovation is everything. ...
read more
Java in Software Product Engineering: The Long-Lasting Edge for ISVs
Aug 28, 2023
Where technologies rise and fall, Java has emerged as a stalwart that stands the test of time....
read more
Best Python Framework for Web Development
Aug 07, 2023
Python web development has emerged as a clear favorite among software developers worldwide....
read more
Mastering Blue-Green Approach with CI/CD for Seamless Deployment
Aug 01, 2023
Continuous integration and continuous deployment (CI/CD) have become indispensable practices in the world of DevOps services, ensuring swift and dependable delivery of software updates. ...
read more
Identify and Overcome your QA Mishaps Before it’s too Late
Aug 26, 2021
The world is in a race to make lives easier. Promising a good experience comes with the added baggage of promising quality. ...
read more
What is API Management, and why do we need api management ?
Jul 09, 2021
The democratization of the internet has enabled and empowered people and businesses to access the required information from anywhere at any time. ...
read more
Must Have Product Engineering Technologies of 2021
Jan 18, 2021
The COVID-19 pandemic has accelerated the digital transformation of organizations, and ISVs must rise to the occasion by upgrading their technologies and building better solutions. ...
read more
Vagrant: Building stronger workflows in DevOps
Mar 05, 2019
In my previous post, I spoke about DevOps in 2019, and the surge that is expected in DevOps practices across the Software Development LifeCycle (SDLC). From here on, we will be taking different DevOps tools and environments which are expected to contribute the most towards the DevOps tool market in 2019.Servers are moving faster...
read more
DevOps in 2019: Tools & Best Practices
Jan 21, 2019
Improving the Software Development Lifecycle (SDLC) from design through development and production is essential for better applications and even better team performance. DevOps is a software engineering practice to improve the SDLC process from design through the development process to production support that unifies Software De...
read more
Entity Framework – What and Why?
Dec 03, 2018
Entity Framework is an open source object relational model framework for the applications built on .NET. It facilitates the developers to work with data without looking into underlying database tables and columns where the data is stored. With Entity Framework in place, developers can now create and maintain data-oriented applic...
read more
What is Digital in Mortgage?
Apr 24, 2017
Digital or Digitalization is an umbrella term for the services using digital technologies, mainly on the Internet, but also including mobile phones, display advertising, and any other digital medium.This is going to be a series of posts on digital mortgage, in the attempt to discuss and give a clear picture of what is the digita...
read more
Sign and Zipalign APK Using Existing Keystore
Mar 02, 2017
Updating an app on Play store is something which is a routine task if you wish to optimize the app and increase usability for the users. When we try to publish an update for an existing app to play store we SHOULD use the existing key store file which we used while initially publishing the app on play store.While trying to achie...
read more
How To: Background jobs in Web Application using Hangfire
Feb 09, 2017
Don’t you not like it one bit when users think that your application is sluggish? And you know that, you really cannot do anything about it, because it is interacting with third party services, tools, vendors, and is just doing way too many tasks and some of them really complex.If you think, the user need not wait for the job to...
read more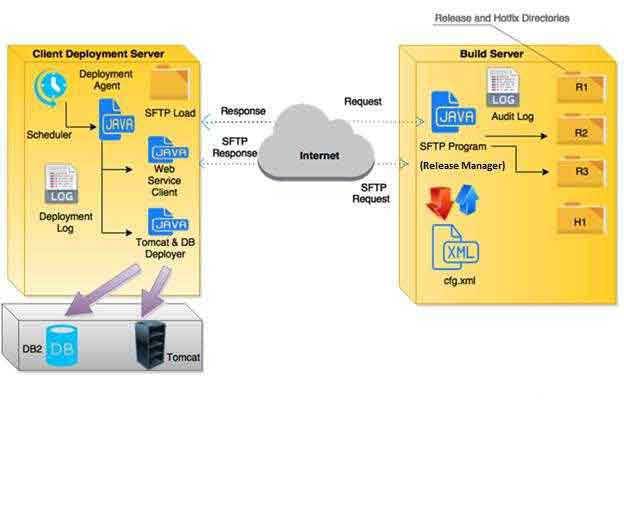
Custom Auto Deployment: A Client – Server Model
Jan 22, 2016
Auto deployment is extremely useful when installations need to be carried out at multiple locations in a quick and effective manner.One of our customers, one of the major ISVs in Behavioral health with over a hundred client installations, were handling many such installations manually. The process in place used deployment via r...
read more
Insecure Direct Object References – Closing the doors
Mar 04, 2015
We have all worked on scenarios where we grant system object access to certain users based on the parameter, provided by them. Sometimes, the user just changes the parameter passed as input intelligently, and she gets access to some restricted documents or db data.For example, you should not be able to see your manager’s review ...
read more
Cross-site Scripting (XSS) - Focus on validation for web applications
Feb 20, 2015
As a part of this security series, I had posted previously about SQL injection, and how this simple concept can manifest itself into a major security concern. This blog post will focus on validation of input and output in a web application.In web-application it has been noticed that we validate the input most of the time. This ...
read more
SQL Injection Explained: A Simple Security Risk
Jan 27, 2015
In my previous blog, I focused on the security issues associated with broken authentication and session management concerns. Here I shall focus on the security and the vulnerability quotient of an application.I will discuss about the threats and their possible solutions. I will also mention few tools that aid the hacker in outs...
read more
Secure Software Product Engineering | Nalashaa Services
Dec 19, 2014
This blog post showcases the need for protecting user’s password, the password habits that the application should enforce to the end user, and the practices that a developer should follow to secure a user’s information, especially the session information. This blog will also focus on aspects of session management.Some key ...
read more